Difference between revisions of "BXadmin:Network"
| (21 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | = | + | There is discussion of network changes related to adding new subnets for Galaxy at [[bxa:Network/Galaxy]] which should be relevant should you need to add a new subnet. |
| − | == 10.1.1.0 /24, 2610:8: == | + | |
| + | = Layer 2 = | ||
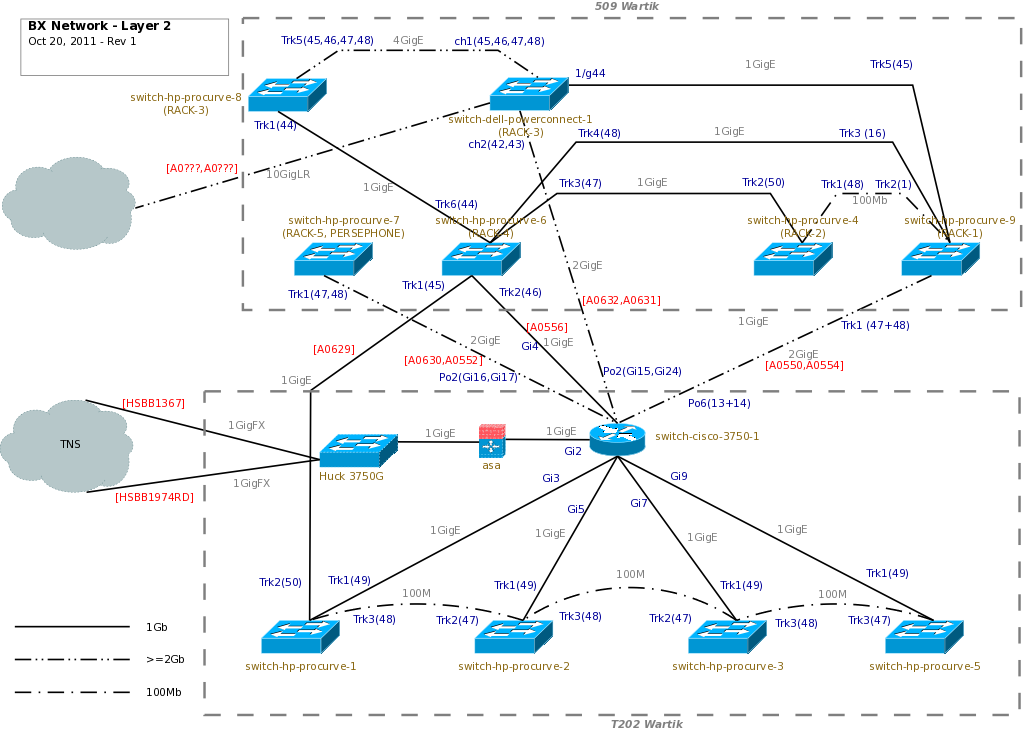
| + | Current network diagram in DIA format is located at /afs/bx.psu.edu/admin/documents/bx_network-l2-<DATE>.dia | ||
| + | |||
| + | When updating, be sure to work on a copy, and update the date in the box in the upper left-hand corner. | ||
| + | |||
| + | [[File:Bx network-l2-2011-10-20.png]] | ||
| + | |||
| + | = Layer 3 = | ||
| + | == VLAN 1 | MANAGEMENT | 10.1.1.0 /24, 2610:8:7800:25:: /64 == | ||
* VLAN: 1 (MANAGEMENT) | * VLAN: 1 (MANAGEMENT) | ||
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
| Line 9: | Line 18: | ||
Switches, IPMI interfaces, ESXi management, etc. | Switches, IPMI interfaces, ESXi management, etc. | ||
| − | == 10.1.2.0 / | + | == VLAN 230 | PRINTERS | 10.1.2.0 /24, 2610:8:7800:2a:: /64 == |
* VLAN: 230 (PRINTERS) | * VLAN: 230 (PRINTERS) | ||
| − | * Netmask: 255.255.255. | + | * Netmask: 255.255.255.0 |
| − | * Broadcast: 10.1.2. | + | * Broadcast: 10.1.2.255 |
* Gateway: 10.1.2.1 | * Gateway: 10.1.2.1 | ||
| − | * Usable IPs: .1 - . | + | * Usable IPs: .1 - .254 |
| − | * Client IPs: | + | * Client IPs: 253 |
* DNS: *.printers.bx.psu.edu | * DNS: *.printers.bx.psu.edu | ||
| − | Printers | + | Printers or other non-management-type devices. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == 10.1.4.0 /24 == | + | == VLAN 200 | PERSEPHONE | 10.1.4.0 /24, 2610:8:7800:2b:: /64 == |
* VLAN: 200 (PERSEPHONE) | * VLAN: 200 (PERSEPHONE) | ||
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
| Line 40: | Line 38: | ||
Persephone cluster. | Persephone cluster. | ||
| − | == 10.1.5.0 /24 == | + | == VLAN 250 | UNAUTH | 10.1.5.0 /24 == |
* VLAN: 250 (UNAUTH) | * VLAN: 250 (UNAUTH) | ||
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
| Line 47: | Line 45: | ||
* DNS: *.unauth.bx.psu.edu | * DNS: *.unauth.bx.psu.edu | ||
| − | Radius dumps unauthorized ports | + | Radius dumps unauthorized ports in this VLAN. DNS blackhole. |
| − | == 10.1.6.0 /24 == | + | == VLAN 260 | QUARANTINE | 10.1.6.0 /24 == |
| − | * VLAN: | + | * VLAN: 260 (QUARANTINE) |
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
* Broadcast: 10.1.6.255 | * Broadcast: 10.1.6.255 | ||
| Line 58: | Line 56: | ||
Radius dumps quanrantined MACs and users in this VLAN. DNS blackhole. | Radius dumps quanrantined MACs and users in this VLAN. DNS blackhole. | ||
| − | == 192.168.2.0 /24 == | + | == VLAN 210 | LINNE | 192.168.2.0 /24 == |
* VLAN: 210 (LINNE) | * VLAN: 210 (LINNE) | ||
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
| Line 67: | Line 65: | ||
linne cluster | linne cluster | ||
| − | == 192.168.4.0 /24 == | + | == VLAN 220 | GALAXY | 192.168.4.0 /24, 2610:8:7800:2c:: /64 == |
* VLAN: 220 (GALAXY) | * VLAN: 220 (GALAXY) | ||
* Netmask: 255.255.255.0 | * Netmask: 255.255.255.0 | ||
| Line 74: | Line 72: | ||
* DNS: *.g2.bx.psu.edu | * DNS: *.g2.bx.psu.edu | ||
| − | galaxy | + | old galaxy private network |
| − | == 128.118.200.0 /23, 2610:8:7800:14:: /64 == | + | == VLAN 270 | GALAXY_PRIVATE | 172.18.2.0 /24 == |
| + | * VLAN: 270 (GALAXY_PRIVATE) | ||
| + | * Netmask: 255.255.255.0 | ||
| + | * Broadcast: 172.18.2.255 | ||
| + | * Gateway: 172.18.2.1 | ||
| + | * DNS: *.g2.bx.psu.edu | ||
| + | |||
| + | Galaxy private addresses. These addresses are registered with TNS and are on the IPv4 Contacts List. | ||
| + | |||
| + | == VLAN 100 | BX-WIRED | 128.118.200.0 /23, 2610:8:7800:14:: /64 == | ||
* VLAN: 100 (BX-WIRED) | * VLAN: 100 (BX-WIRED) | ||
* Netmask: 255.255.254.0 | * Netmask: 255.255.254.0 | ||
| Line 84: | Line 91: | ||
Centrally managed machines. Machines that we have root on and/or control with cfengine. | Centrally managed machines. Machines that we have root on and/or control with cfengine. | ||
| − | == 128.118.202. | + | == VLAN 110 | DOT1X | 128.118.202.128 /25, 2610:8:7800:28:: /64 == |
* VLAN: 110 (DOT1X) | * VLAN: 110 (DOT1X) | ||
| − | * Netmask: 255.255.255. | + | * Netmask: 255.255.255.128 |
| − | * Broadcast: 128.118.202. | + | * Broadcast: 128.118.202.255 |
| − | * Gateway: 128.118.202. | + | * Gateway: 128.118.202.129 |
| − | |||
| − | |||
* DNS: dot1x-128-118-202-N.bx.psu.edu | * DNS: dot1x-128-118-202-N.bx.psu.edu | ||
| + | |||
| + | === PAT Address | 128.118.202.254 === | ||
| + | PAT = Port Address Translation. This is similar to how SNAT works with iptables. A single public ip. This is preferred to just straight NAT, which on the ASA is one-to-one with a set translation expiration time. After the global IP range is used up, further outbound connections are dropped. A single PAT address supports up to 65,536 outbound connections (TCP sessions). | ||
| + | |||
| + | NAT config on ASA: | ||
| + | <pre>global (Outside) 1 128.118.202.254 | ||
| + | nat (Bioinformatics) 1 192.168.2.0 255.255.255.0 | ||
| + | nat (Bioinformatics) 1 192.168.4.0 255.255.255.0 | ||
| + | nat (Bioinformatics) 1 10.1.0.0 255.255.0.0 | ||
| + | </pre> | ||
Dynamically assigned with DHCP. 802.1x EAP-TTLS-PAP username/password login. | Dynamically assigned with DHCP. 802.1x EAP-TTLS-PAP username/password login. | ||
| − | == 128.118.202.64 | + | == VLAN 120 | UNMANAGED | 128.118.202.0 /25, 2610:8:7800:29:: /64 == |
* VLAN: 120 (UNMANAGED) | * VLAN: 120 (UNMANAGED) | ||
| − | * Netmask: 255.255.255. | + | * Netmask: 255.255.255.128 |
* Broadcast: 128.118.202.127 | * Broadcast: 128.118.202.127 | ||
| − | * Gateway: 128.118.202. | + | * Gateway: 128.118.202.1 |
| − | |||
| − | |||
* DNS: custom or 128-118-202-N.bx.psu.edu | * DNS: custom or 128-118-202-N.bx.psu.edu | ||
Statically assgined with DHCP based on MAC. Radius attributes defined in LDAP for the DHCP host entry. | Statically assgined with DHCP based on MAC. Radius attributes defined in LDAP for the DHCP host entry. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | == VLAN 130 | GUEST | ? == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == | ||
* VLAN: 130 (GUEST) | * VLAN: 130 (GUEST) | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
* DNS: guest-128-118-202-N.bx.psu.edu | * DNS: guest-128-118-202-N.bx.psu.edu | ||
DHCP entries static in LDAP. Web authorization form to allow changing of the MAC address, restricted to PIs and other persons of repute. These entries will be periodically expired. Or, tie into EDUROAM somehow? | DHCP entries static in LDAP. Web authorization form to allow changing of the MAC address, restricted to PIs and other persons of repute. These entries will be periodically expired. Or, tie into EDUROAM somehow? | ||
| − | = | + | Not sure what addresses GUEST will use, or if it will be NAT'd. |
| − | + | ||
| + | == VLAN 140 | GALAXY_PUBLIC | 128.118.79.224 /27 == | ||
| + | * VLAN: 140 (BX-WIRED) | ||
| + | * Netmask: 255.255.255.224 | ||
| + | * Broadcast: 128.118.79.255 | ||
| + | * Gateway: 128.118.79.225 | ||
| + | |||
| + | Galaxy public addresses. This network can route on the XSEDE network via switch-dell-powerconnect-1. | ||
| + | |||
| + | == VLAN 500 | RCC_P2P | 10.128.255.240/29 == | ||
| + | * VLAN: 500 (RCC_P2P) | ||
| + | * Netmask 255.255.255.248 | ||
| + | Point to point with RCC. | ||
| + | |||
| + | switch-dell-powerconnect-1: | ||
| + | <pre>interface vlan 500 | ||
| + | name "RCC_P2P" | ||
| + | routing | ||
| + | ip address 10.128.255.241 255.255.255.248 | ||
| + | exit | ||
| + | </pre> | ||
| + | |||
| + | VLAN 500 is untagged on access port 1/xg1 | ||
| + | |||
| + | == VLAN 510 | CISCO_DELL_P2P | 10.1.7.0/29 == | ||
| + | * VLAN: 510 (CISCO_DELL_P2P) | ||
| + | * Netmask 255.255.255.248 | ||
| + | |||
| + | cisco vlan 510 : 10.1.7.1 | ||
| + | dell vlan 510 : 10.1.7.2 | ||
| + | |||
| + | = Spanning Tree = | ||
| + | |||
| + | We are using MSTP, with a single region. | ||
| + | |||
| + | '''Configuration Name:''' MST | ||
| + | |||
| + | == MSTI 0 (IST) == | ||
| + | * MANAGEMENT | ||
| + | * Root: switch-cisco-3750-1 | ||
| + | * Mapped VLANs: 1 | ||
| + | |||
| + | == MSTI 1 == | ||
| + | * BX-WIRED, DOT1X, UNMANAGED | ||
| + | * Root: switch-cisco-3750-1 | ||
| + | * Mapped VLANs: 100, 110, 120 | ||
| + | |||
| + | == MSTI 2 == | ||
| + | * PRINTERS, UNAUTH, QUARANTINE | ||
| + | * Root: switch-cisco-3750-1 | ||
| + | * Mapped VLANs: 230, 250, 260 | ||
| + | |||
| + | == MSTI 3 == | ||
| + | * PERSEPHONE, LINNE | ||
| + | * Root: switch-hp-procurve-7 | ||
| + | * Mapped VLANs: 200, 210 | ||
| + | |||
| + | == MSTI 4 == | ||
| + | * GALAXY | ||
| + | * Root: switch-dell-powerconnect-1 | ||
| + | * Mapped VLANs: 220 | ||
| − | + | == MSTI 5 == | |
| + | * CISCO_DELL_P2P | ||
| + | * Root: switch-dell-powerconnect-1 | ||
| + | * Mapped VLANs: 510 | ||
| − | + | == MSTI 6 == | |
| + | * DELL_RCC | ||
| + | * Root: switch-dell-powerconnect-1 | ||
| + | * Mapped VLANs: 500 | ||
Latest revision as of 16:14, 21 February 2012
There is discussion of network changes related to adding new subnets for Galaxy at bxa:Network/Galaxy which should be relevant should you need to add a new subnet.
Contents
- 1 Layer 2
- 2 Layer 3
- 2.1 VLAN 1 | MANAGEMENT | 10.1.1.0 /24, 2610:8:7800:25:: /64
- 2.2 VLAN 230 | PRINTERS | 10.1.2.0 /24, 2610:8:7800:2a:: /64
- 2.3 VLAN 200 | PERSEPHONE | 10.1.4.0 /24, 2610:8:7800:2b:: /64
- 2.4 VLAN 250 | UNAUTH | 10.1.5.0 /24
- 2.5 VLAN 260 | QUARANTINE | 10.1.6.0 /24
- 2.6 VLAN 210 | LINNE | 192.168.2.0 /24
- 2.7 VLAN 220 | GALAXY | 192.168.4.0 /24, 2610:8:7800:2c:: /64
- 2.8 VLAN 270 | GALAXY_PRIVATE | 172.18.2.0 /24
- 2.9 VLAN 100 | BX-WIRED | 128.118.200.0 /23, 2610:8:7800:14:: /64
- 2.10 VLAN 110 | DOT1X | 128.118.202.128 /25, 2610:8:7800:28:: /64
- 2.11 VLAN 120 | UNMANAGED | 128.118.202.0 /25, 2610:8:7800:29:: /64
- 2.12 VLAN 130 | GUEST | ?
- 2.13 VLAN 140 | GALAXY_PUBLIC | 128.118.79.224 /27
- 2.14 VLAN 500 | RCC_P2P | 10.128.255.240/29
- 2.15 VLAN 510 | CISCO_DELL_P2P | 10.1.7.0/29
- 3 Spanning Tree
Layer 2
Current network diagram in DIA format is located at /afs/bx.psu.edu/admin/documents/bx_network-l2-<DATE>.dia
When updating, be sure to work on a copy, and update the date in the box in the upper left-hand corner.
Layer 3
VLAN 1 | MANAGEMENT | 10.1.1.0 /24, 2610:8:7800:25:: /64
- VLAN: 1 (MANAGEMENT)
- Netmask: 255.255.255.0
- Broadcast: 10.1.1.255
- Gateway: 10.1.1.1
- DNS: *.net.bx.psu.edu
Switches, IPMI interfaces, ESXi management, etc.
VLAN 230 | PRINTERS | 10.1.2.0 /24, 2610:8:7800:2a:: /64
- VLAN: 230 (PRINTERS)
- Netmask: 255.255.255.0
- Broadcast: 10.1.2.255
- Gateway: 10.1.2.1
- Usable IPs: .1 - .254
- Client IPs: 253
- DNS: *.printers.bx.psu.edu
Printers or other non-management-type devices.
VLAN 200 | PERSEPHONE | 10.1.4.0 /24, 2610:8:7800:2b:: /64
- VLAN: 200 (PERSEPHONE)
- Netmask: 255.255.255.0
- Broadcast: 10.1.4.255
- Gateway: 10.1.4.1
- DNS: *.persephone.bx.psu.edu
Persephone cluster.
VLAN 250 | UNAUTH | 10.1.5.0 /24
- VLAN: 250 (UNAUTH)
- Netmask: 255.255.255.0
- Broadcast: 10.1.5.255
- Gateway: 10.1.5.1
- DNS: *.unauth.bx.psu.edu
Radius dumps unauthorized ports in this VLAN. DNS blackhole.
VLAN 260 | QUARANTINE | 10.1.6.0 /24
- VLAN: 260 (QUARANTINE)
- Netmask: 255.255.255.0
- Broadcast: 10.1.6.255
- Gateway: 10.1.6.1
- DNS: *.quarantine.bx.psu.edu
Radius dumps quanrantined MACs and users in this VLAN. DNS blackhole.
VLAN 210 | LINNE | 192.168.2.0 /24
- VLAN: 210 (LINNE)
- Netmask: 255.255.255.0
- Broadcast: 192.168.2.255
- Gateway: 192.168.2.253
- DNS: *.linne.bx.psu.edu
linne cluster
VLAN 220 | GALAXY | 192.168.4.0 /24, 2610:8:7800:2c:: /64
- VLAN: 220 (GALAXY)
- Netmask: 255.255.255.0
- Broadcast: 192.168.4.255
- Gateway: 192.168.2.254
- DNS: *.g2.bx.psu.edu
old galaxy private network
VLAN 270 | GALAXY_PRIVATE | 172.18.2.0 /24
- VLAN: 270 (GALAXY_PRIVATE)
- Netmask: 255.255.255.0
- Broadcast: 172.18.2.255
- Gateway: 172.18.2.1
- DNS: *.g2.bx.psu.edu
Galaxy private addresses. These addresses are registered with TNS and are on the IPv4 Contacts List.
VLAN 100 | BX-WIRED | 128.118.200.0 /23, 2610:8:7800:14:: /64
- VLAN: 100 (BX-WIRED)
- Netmask: 255.255.254.0
- Broadcast: 128.118.201.255
- Gateway: 128.118.200.1, 2610:8:7800:14::1
Centrally managed machines. Machines that we have root on and/or control with cfengine.
VLAN 110 | DOT1X | 128.118.202.128 /25, 2610:8:7800:28:: /64
- VLAN: 110 (DOT1X)
- Netmask: 255.255.255.128
- Broadcast: 128.118.202.255
- Gateway: 128.118.202.129
- DNS: dot1x-128-118-202-N.bx.psu.edu
PAT Address | 128.118.202.254
PAT = Port Address Translation. This is similar to how SNAT works with iptables. A single public ip. This is preferred to just straight NAT, which on the ASA is one-to-one with a set translation expiration time. After the global IP range is used up, further outbound connections are dropped. A single PAT address supports up to 65,536 outbound connections (TCP sessions).
NAT config on ASA:
global (Outside) 1 128.118.202.254 nat (Bioinformatics) 1 192.168.2.0 255.255.255.0 nat (Bioinformatics) 1 192.168.4.0 255.255.255.0 nat (Bioinformatics) 1 10.1.0.0 255.255.0.0
Dynamically assigned with DHCP. 802.1x EAP-TTLS-PAP username/password login.
VLAN 120 | UNMANAGED | 128.118.202.0 /25, 2610:8:7800:29:: /64
- VLAN: 120 (UNMANAGED)
- Netmask: 255.255.255.128
- Broadcast: 128.118.202.127
- Gateway: 128.118.202.1
- DNS: custom or 128-118-202-N.bx.psu.edu
Statically assgined with DHCP based on MAC. Radius attributes defined in LDAP for the DHCP host entry.
VLAN 130 | GUEST | ?
- VLAN: 130 (GUEST)
- DNS: guest-128-118-202-N.bx.psu.edu
DHCP entries static in LDAP. Web authorization form to allow changing of the MAC address, restricted to PIs and other persons of repute. These entries will be periodically expired. Or, tie into EDUROAM somehow?
Not sure what addresses GUEST will use, or if it will be NAT'd.
VLAN 140 | GALAXY_PUBLIC | 128.118.79.224 /27
- VLAN: 140 (BX-WIRED)
- Netmask: 255.255.255.224
- Broadcast: 128.118.79.255
- Gateway: 128.118.79.225
Galaxy public addresses. This network can route on the XSEDE network via switch-dell-powerconnect-1.
VLAN 500 | RCC_P2P | 10.128.255.240/29
- VLAN: 500 (RCC_P2P)
- Netmask 255.255.255.248
Point to point with RCC.
switch-dell-powerconnect-1:
interface vlan 500 name "RCC_P2P" routing ip address 10.128.255.241 255.255.255.248 exit
VLAN 500 is untagged on access port 1/xg1
VLAN 510 | CISCO_DELL_P2P | 10.1.7.0/29
- VLAN: 510 (CISCO_DELL_P2P)
- Netmask 255.255.255.248
cisco vlan 510 : 10.1.7.1 dell vlan 510 : 10.1.7.2
Spanning Tree
We are using MSTP, with a single region.
Configuration Name: MST
MSTI 0 (IST)
- MANAGEMENT
- Root: switch-cisco-3750-1
- Mapped VLANs: 1
MSTI 1
- BX-WIRED, DOT1X, UNMANAGED
- Root: switch-cisco-3750-1
- Mapped VLANs: 100, 110, 120
MSTI 2
- PRINTERS, UNAUTH, QUARANTINE
- Root: switch-cisco-3750-1
- Mapped VLANs: 230, 250, 260
MSTI 3
- PERSEPHONE, LINNE
- Root: switch-hp-procurve-7
- Mapped VLANs: 200, 210
MSTI 4
- GALAXY
- Root: switch-dell-powerconnect-1
- Mapped VLANs: 220
MSTI 5
- CISCO_DELL_P2P
- Root: switch-dell-powerconnect-1
- Mapped VLANs: 510
MSTI 6
- DELL_RCC
- Root: switch-dell-powerconnect-1
- Mapped VLANs: 500